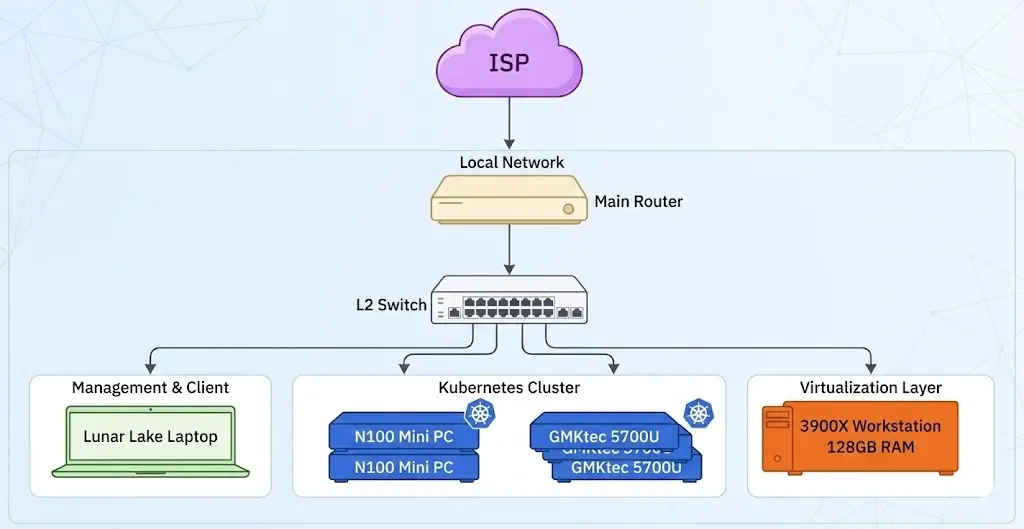
Goal Ship a credible, single-node lab that mirrors an enterprise edge: Proxmox + OVS bridging, pfSense for routing/VLANs, and Security Onion with a SPAN feed for SIEM-grade visibility.
What you’ll build
- pfSense VM providing WAN/LAN, VLAN10 (Users), VLAN20 (Infra), and DHCP.
- Open vSwitch (ovs-br0) on Proxmox with a port-mirror to feed Security Onion’s sensor NIC.
- Security Onion VM with separate mgmt/sensor vNICs to collect mirrored traffic.
Prereqs
- One Proxmox host with VT-x/AMD-V, 4c/16GB free recommended.
- Two physical NICs (WAN1 optional, WAN2 for uplink) or one NIC plus VLAN trunk from your router.
- ISO images: pfSense CE/Plus, Security Onion.
- Proxmox shell access (root) and permission to install openvswitch.
Reference layout (Mermaid)
flowchart LR subgraph PHY["Physical NICs"] direction LR WAN1["WAN1 - Physical NIC - proxmox Connect IP"] WAN2["WAN2 - Physical NIC"] end subgraph OVS["Open vSwitch OVS"] direction TB OVSBR["ovs-br0"] MIRROR["OVS Port Mirror SPAN"] end subgraph VNIC["Virtual NICs"] direction LR LANv["LAN - Virtual NIC\nBridge to VMs"] end subgraph PMX["Proxmox Host"] direction TB PHY OVS VNIC end subgraph PFS["pfSense VM"] direction TB PFSWAN2["WAN2 - vNIC"] PFSLAN["LAN - VLAN Tagging"] SW["pfSense"] end subgraph SO["Security Onion VM"] direction TB SO_MGMT["Manage"] SO_SNIFF["Sensor"] end subgraph VLANS["Separated Networks VLANs"] direction TB VLAN10["VLAN 10 - Users"] VLAN20["VLAN 20 - infra"] end WAN2 --> OVSBR LANv --> OVSBR OVSBR --> MIRROR & PFSWAN2 & PFSLAN PFSWAN2 --> SW PFSLAN --> SW INTERNET["Internet"] --> WAN2 SW -- Vlan Tagged --> VLAN10 & VLAN20 MIRROR -- Mirrored Traffic SPAN --> SO_SNIFF VLAN10 -. mgmt reach .-> SO_MGMT VLAN20 -- Mgmt Access optional --> SO_MGMT SO_SNIFF -- Sensor log --> SO_MGMT style MIRROR stroke:#D50000,fill:#FFD600
Topology summary: vmbr0 = WAN uplink, vmbr1 = WAN passthrough, vmbr2 = VLAN10/20 trunk, mirror output → Security Onion net1 (untagged).
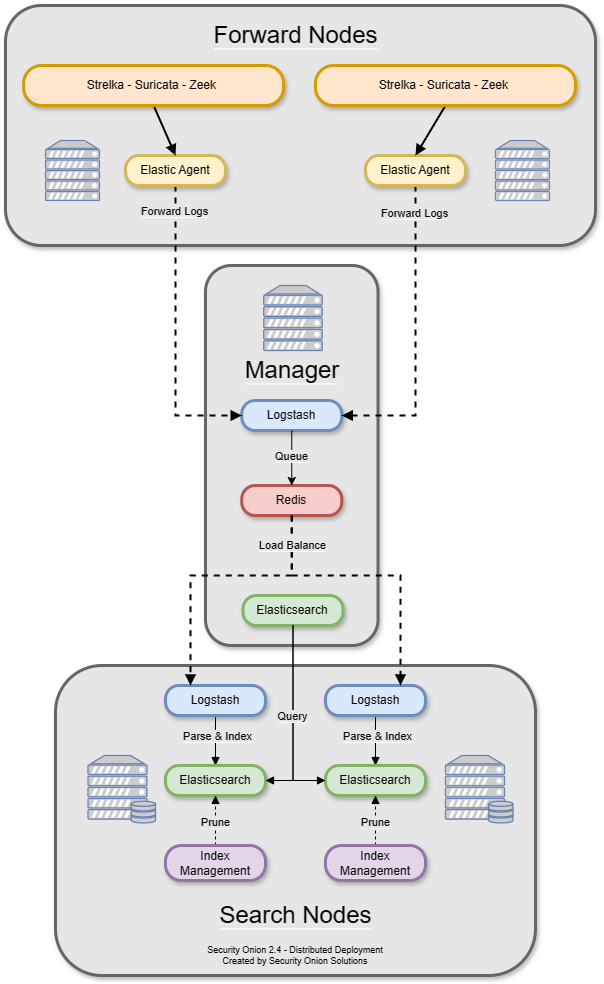
Security Onion reference architecture (vendor diagram)